05 Aug 2022
Digital Identity & Cloud IAM Services

An overview of identity & access management for your organization for your Software as a Service (SaaS) platform or business service that is available on the market today. Understanding what to look for based on functionality, features, price, ongoing support & future development.
We will review the security practice & certifications in the field of security that you will need to manage the security in the identity space within your organization & what are the top-rank services from Gartner insights.
Identity and Access Management (IAM)
Identity and Access Management (IAM) is the ability to provision, manage, audit, and secure digital identities to facilitate and enable approved, authentic requests or connections to view company data, services, systems, networks, and assets.
This applies whether they are located on-premises or in the cloud, based on roles and privileges assigned to each digital identity, both human and machine.
Digital identities are the foundation of a digital society. It is important to first understand some of the terminologies that are related to building digital identity and digital trust.
Digital Identity
Digital identities have been growing in popularity and implementation over the past few years, especially within national governments. Some countries that have implemented digital identities include Belgium, Cameroon, Canada, Ecuador, Estonia, France, Jordan, Kyrgyzstan, Italy, Iran, Japan, Senegal, and Thailand.
And here in Australia, your digital identity makes accessing government services online simple, safer and more secure, which is managed within the myGovID website. Most of Australia may have visited this site as part of the COVID pandemic at some stage
For more information
https://www.digitalidentity.gov.au/
https://www.mygovid.gov.au/
Mckinsey reports - To date, governments around the world have launched around 165 digital, or partially digital, ID schemes. However, their track record is mixed. Only a few programs have achieved high levels of adoption, and use rates are often low, averaging just once or twice a year per person in some countries.
Digital identity in Australia is used by residents to validate who they are over digital media, such as over the Internet.
While many organisations use their own mechanisms, increasingly, aggregated digital identities are in use. Many Australian organisations leverage popular ubiquitous Internet identities such as those provided by social login services including Facebook, Google, Twitter and LinkedIn to perform the following functions:
Single sign-on to help users avoid creating new usernames and passwords for each site.
- To provide some basic validation of identity
- To provide some integration, especially with social media, e-mail and contacts
- To identify the natural person behind a transaction for statutory purposes such as a monetary transfer
Ref - Digital identity in Australia - Wikipedia
Identity Services Companies
- Azure Active Directory
- Saviynt
- Okta
- auth0
- jumpcloud
- PingIdentitiy
- OneLogin
- ForgeRock
- IBM
- Oracle
- CyberArk
- Iiantus
- datawiza
Solutions to look for when selecting a Cloud Identity Service
- Identity management
- Directory Integration
- Group Management
- Single Sign-On
- Device Management
- Multi-Factor Authentication (MFA)
- API Integration
- Customization & Implementation of UI UX
An overview of Identity Terminology
- Access Management – the process of managing user access to resources
- Authentication – The process of verifying a digital identity
- Authorization – The process of verifying a digital identity should have access to a service or resource
- Attributes – information associated with the digital identity such as name, address, location, or number
- Credentials – information that pertains to the integrity of identity attributes such as a username or password also known as a Secret
- Data Brokers – the entity responsible for managing access to data
- Identification – The process of determining which attributes are gathered and verified for accuracy
- Identity Proofing – the process of uniquely identifying the user, validating authenticity, checking the accuracy, and verification of the claim at the time of authentication
- Level of Assurance – the confidence level that the identity is authentic such as the security controls satisfied during authentication
- Level of Trust – the process of determining business risk exposure and whether more security control must be satisfied
- Privilege – the level of access authorization that allows access and entitlement for a group or user
Support
It’s recommended to review the tech & development support that is available for free. Then review what support is based on the pricing modelling.
Pricing Modelling
It’s critical that you need to understand, all will be different but similar.
- Some will be based on user you pay for each user added to your account.
- Added cost will also be based on the features you add to your subscription.
- Some may have a trial/package base modelling, which may also provide a discount, but you may be paying for a feature you do not need.
- And monthly or Annual payment same may provide a discount if you pay annually.
Gartner - Identity and Access Management (IAM)
- Identity and access management (IAM) is the discipline that enables the right individuals to access the right resources at the right times for the right reasons.
- IAM addresses the mission-critical need to ensure appropriate access to resources across increasingly heterogeneous technology environments and to meet increasingly rigorous compliance requirements. IAM is a crucial undertaking for any enterprise. It is increasingly business-aligned, and it requires business skills, not just technical expertise.
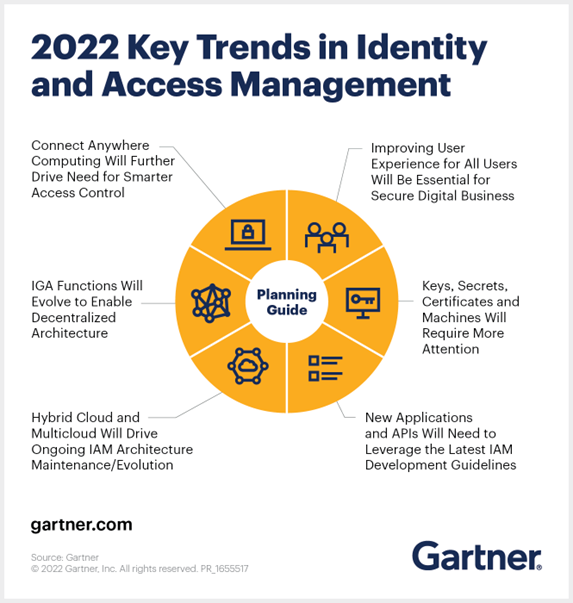
Enterprises that develop mature IAM capabilities can reduce their identity management costs and, more importantly, become significantly more agile in supporting new business initiatives.
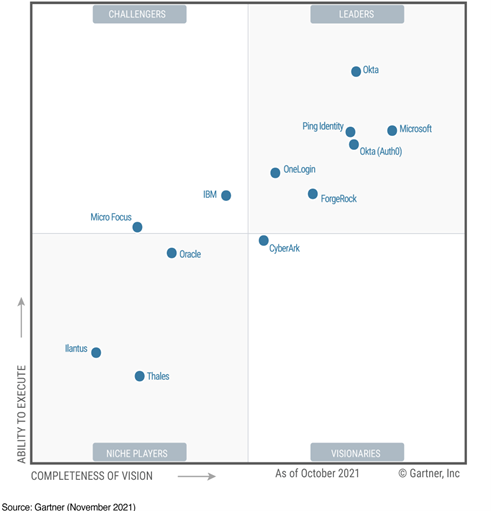
Microsoft is a 5-time Leader in the Gartner Magic Quadrant for Access Management
Gartner Magic Quadrant for Access Management
See below
Access management has become the source of trust for identity-first security. Increased dependence on identities for access anywhere, anytime, requires AM to be more reliable and easier to adopt. Identity orchestration, IAM convergence and SaaS resilience importance will increase during 2022.
Ref
https://www.gartner.com/doc/reprints?id=1-27UADDR3&ct=211102&st=sb
Kerberos Authentication Overview
Kerberos is an authentication protocol that is used to verify the identity of a user or host. This topic contains information about Kerberos authentication in Windows Server 2012 and Windows 8.
https://docs.microsoft.com/en-us/windows-server/security/kerberos/kerberos-authentication-overview
Essential Eight Maturity Model
The Australian Cyber Security Centre (ACSC) has developed prioritised mitigation strategies, in the form of the Strategies to Mitigate Cyber Security Incidents, to help organisations protect themselves against various cyber threats. The most effective of these mitigation strategies are the Essential Eight.
Security Certifications
- CISSP
- CompTIA Security+
- Microsoft Security Certification Series – SC-200, SC-300, SC-400, SC-900 or MS-500/ AZ-500
Browse Certifications and Exams | Microsoft Docs
Introducing Microsoft’s New Security Certifications - Microsoft Tech Community