Is your Security Operations Centre ( SOC ) meeting the requirement your business needs?
What is security incident and event management (SIEM)?
A SIEM system is a tool that an organization uses to collect, analyze, and perform security operations on its computer systems. Those systems can be hardware appliances, applications, or both.
In its simplest form, a SIEM system enables you to:
- Collect and query logs.
- Do some form of correlation or anomaly detection.
- Create alerts and incidents based on your findings.
A SIEM system might offer functionality such as:
-
Log management: The ability to collect, store, and query the log data from resources within your environment.
-
Alerting: A proactive look inside the log data for potential security incidents and anomalies.
-
Visualization: Graphs and dashboards that provide visual insights into your log data.
-
Incident management: The ability to create, update, assign, and investigate incidents that have been identified.
-
Querying data: A rich query language, similar to that for log management, that you can use to query and understand your data.
What is Microsoft Sentinel?
Azure Sentinel is a cloud-native SIEM system that a security operations team can use to:
- Get security insights across the enterprise by collecting data from virtually any source.
- Detect and investigate threats quickly by using built-in machine learning and Microsoft threat intelligence.
- Automate threat responses by using playbooks and by integrating Azure Logic Apps.
Unlike with traditional SIEM solutions, to run Microsoft Sentinel, you don't need to install any servers either on-premises or in the cloud. Microsoft Sentinel is a service that you deploy in Azure. You can get up and running with Sentinel in just a few minutes in the Azure portal.
Microsoft Sentinel is tightly integrated with other cloud services. Not only can you quickly ingest logs, but you can also use other cloud services natively (for example, authorization and automation).
Microsoft Sentinel helps you enable end-to-end security operations including collection, detection, investigation, and response:

How Microsoft Sentinel works
As you've already learned, Microsoft Sentinel helps you enable end-to-end security operations. It starts with log ingestion and continues through to automated response to security alerts.
Here are the key features and components of Microsoft Sentinel.
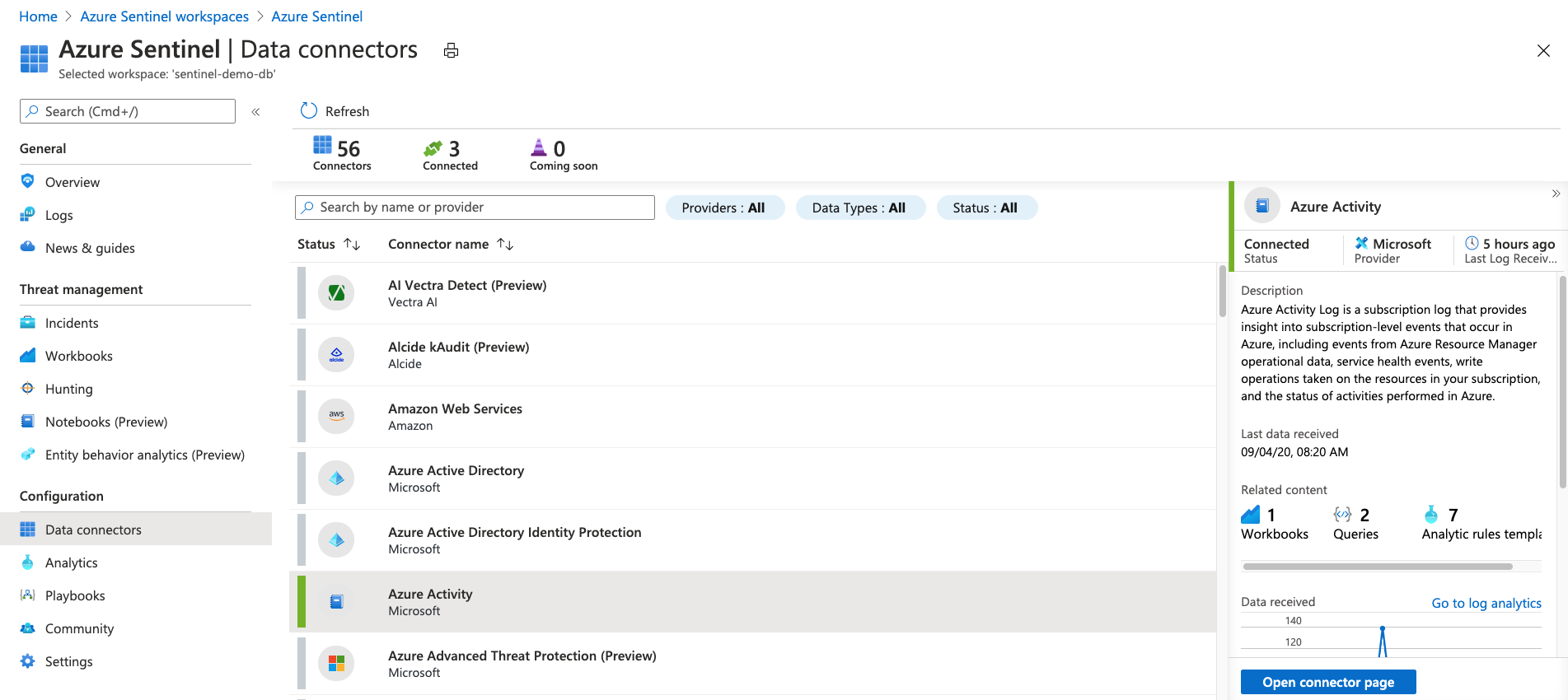
Data connectors
The first thing to do is to have your data ingested into Microsoft Sentinel. Data connectors enable you to do just that. You can add some services, such as Azure activity logs, just by selecting a button. Others, such as syslog, require a little configuration. There are data connectors that cover all scenarios and sources, including but not limited to:
- syslog
- Common Event Format (CEF)
- Trusted Automated eXchange of Indicator Information (TAXII) (for threat intelligence)
- Azure
- AWS services
Log retention
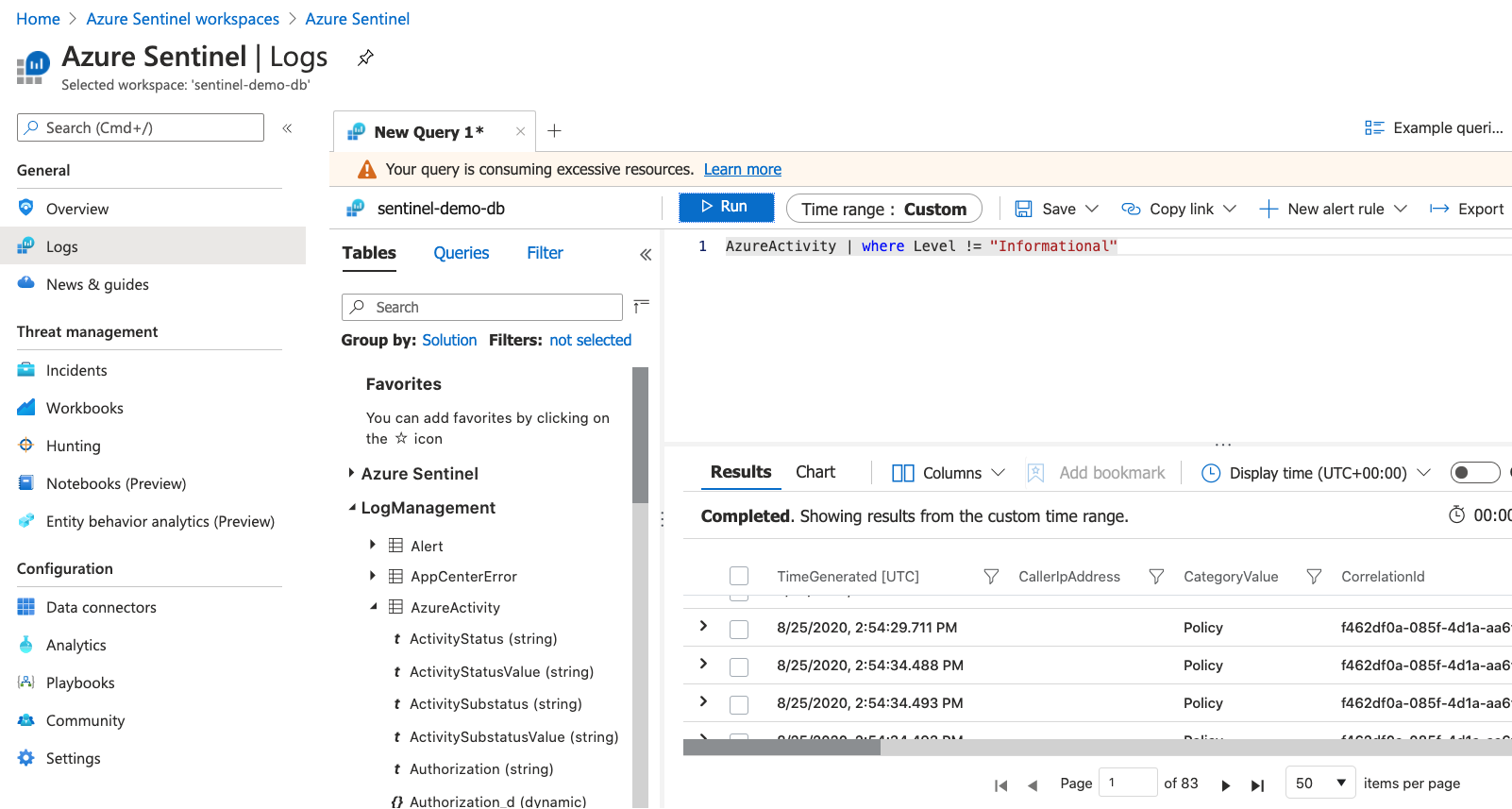
After it's been ingested into Microsoft Sentinel, your data is stored by using Log Analytics. The benefits of using Log Analytics include the ability to use the Kusto Query Language (KQL) to query your data. KQL is a rich query language that gives you the power to dive into and gain insights from our data.
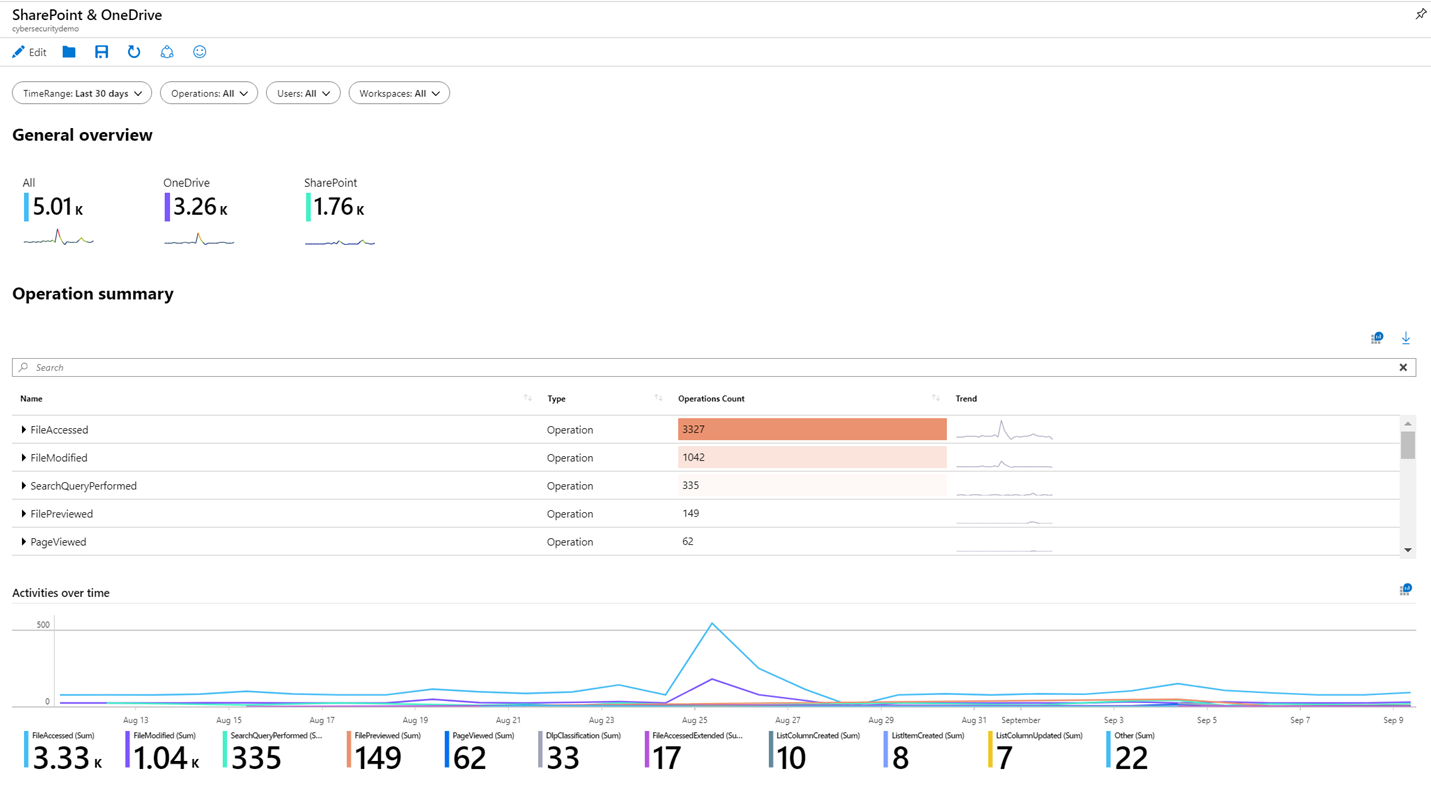
Workbooks
You use workbooks to visualize your data within Microsoft Sentinel. Think of workbooks as dashboards. Each component in the dashboard is built by using an underlying KQL query of your data. You can use the built-in workbooks within Microsoft Sentinel, edit them to meet your own needs, or create your own workbooks from scratch. If you've used Azure Monitor workbooks, this feature will be familiar to you because it's Sentinel's implementation of Monitor workbooks.
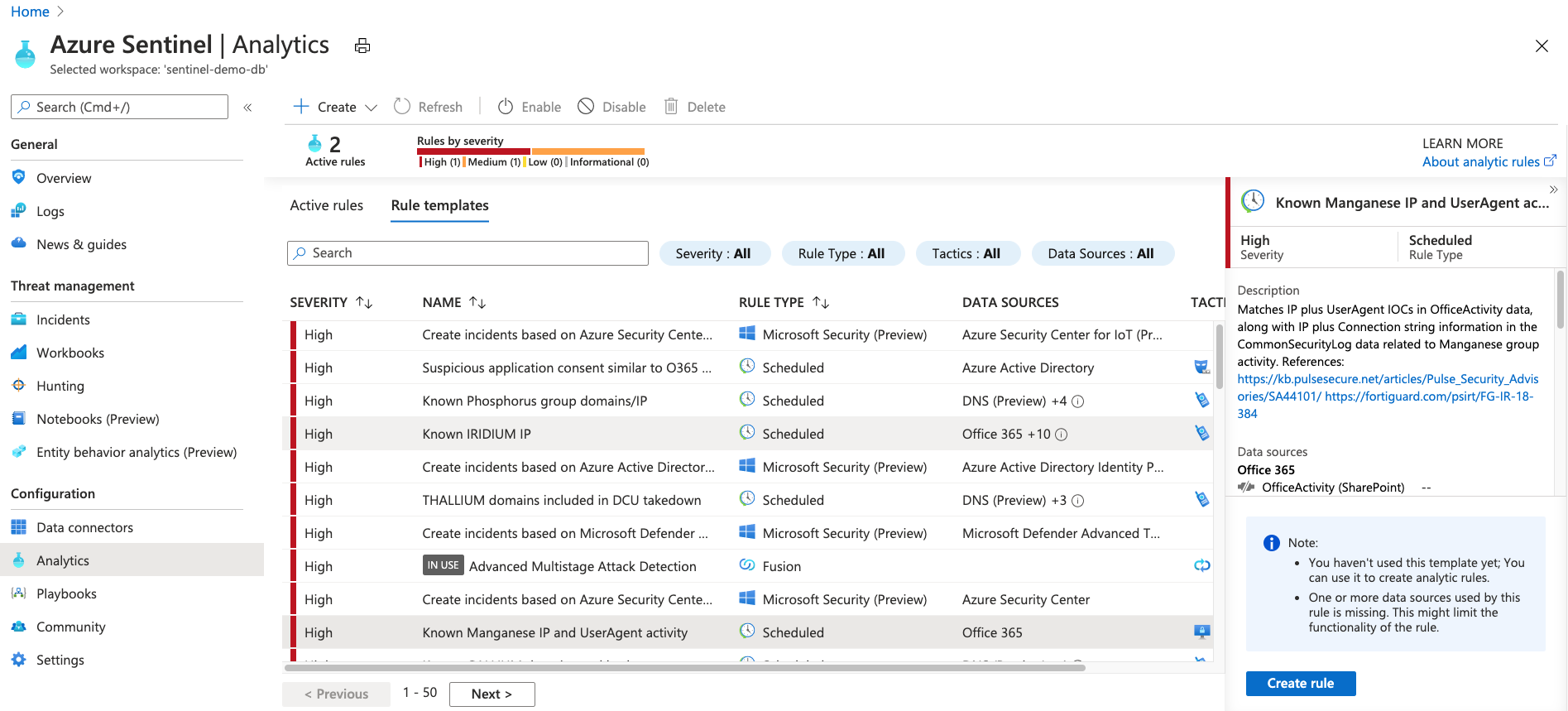
Analytics alerts
So far, you have your logs and some data visualization. Now it would be great to have some proactive analytics across your data, so you're notified when something suspicious occurs. You can enable built-in analytics alerts within your Sentinel workspace. There are various types of alerts, some of which you can edit to your own needs. Other alerts are built on machine-learning models that are proprietary to Microsoft. You can also create custom, scheduled alerts from scratch.
Threat hunting
We won't dive deeply into threat hunting, however, if SOC analysts need to hunt for suspicious activity, there are some built-in hunting queries that they can use. Analysts can also create their own queries. Sentinel also integrates with Azure Notebooks. It provides example notebooks for advanced hunters who want to use the full power of a programming language to hunt through their data.
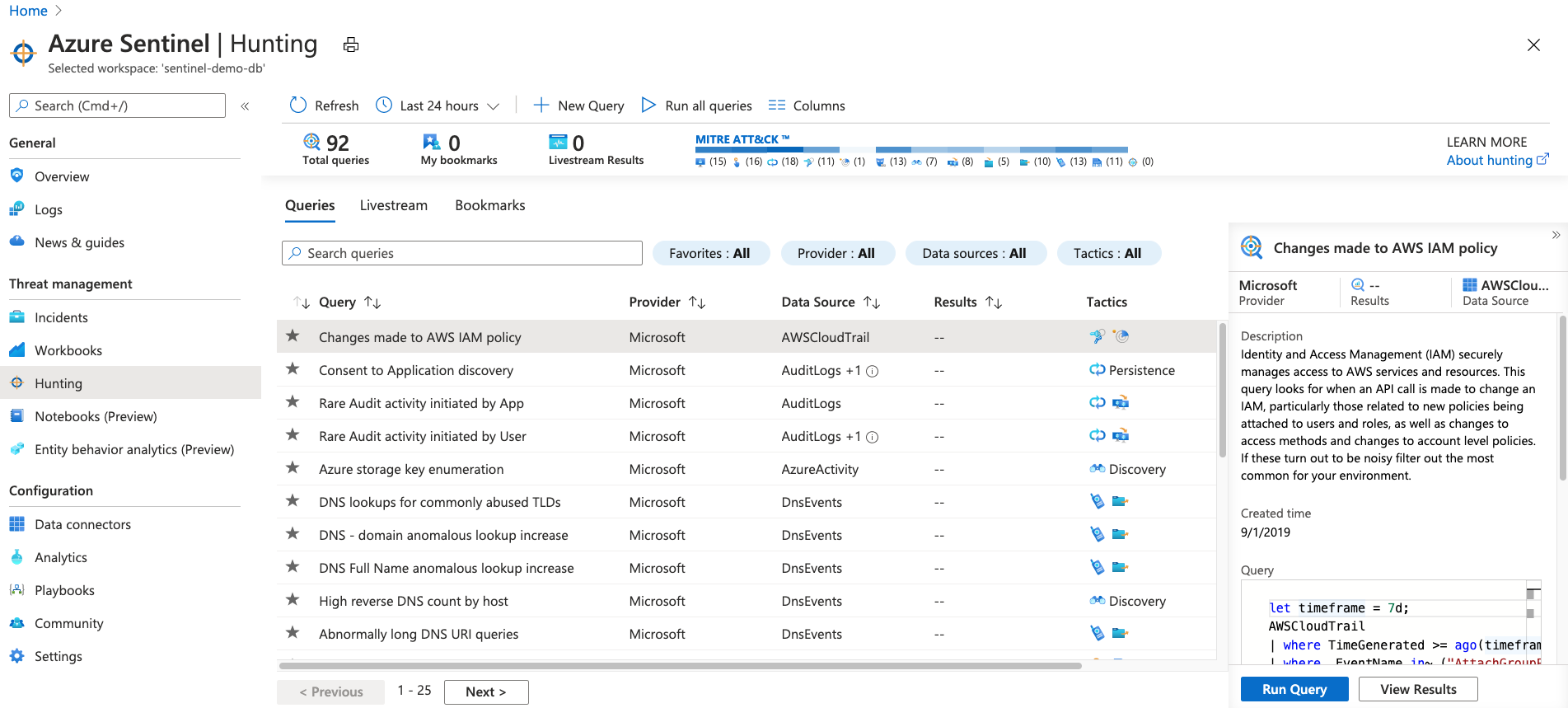
Incidents and investigations
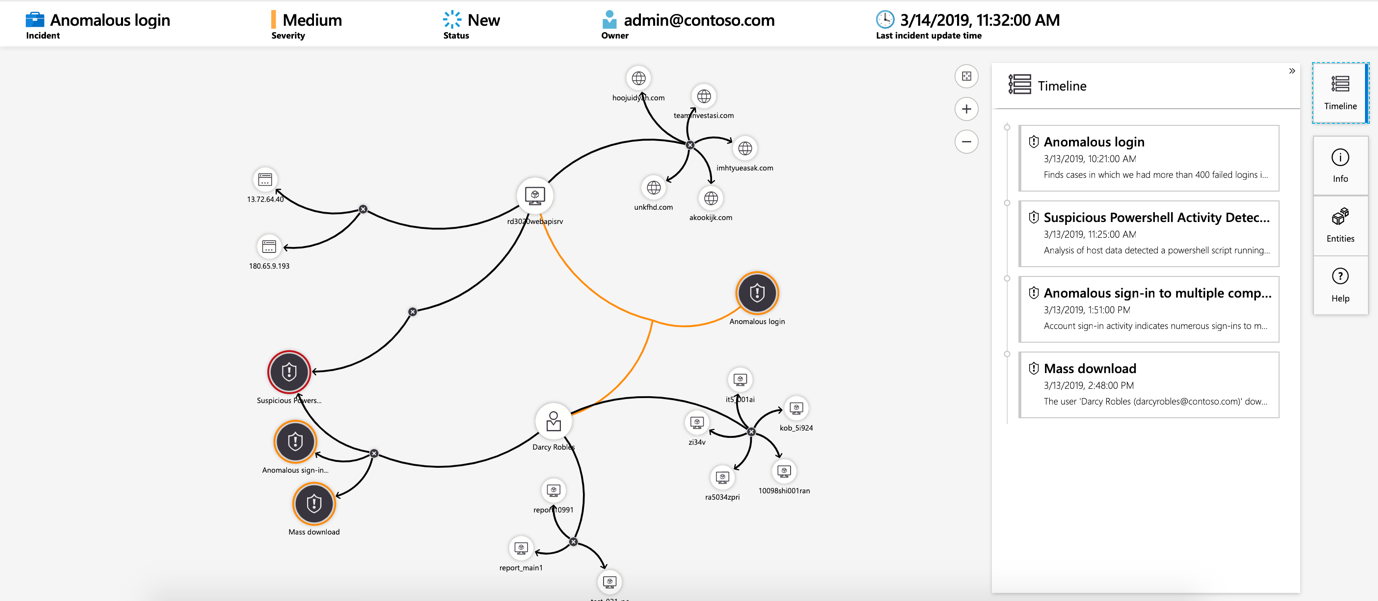
An incident is created when an alert that you've enabled is triggered. In Microsoft Sentinel, you can do standard incident management tasks like changing status or assigning incidents to individuals for investigation. Microsoft Sentinel also has investigation functionality, so you can visually investigate incidents by mapping entities across log data along a timeline.
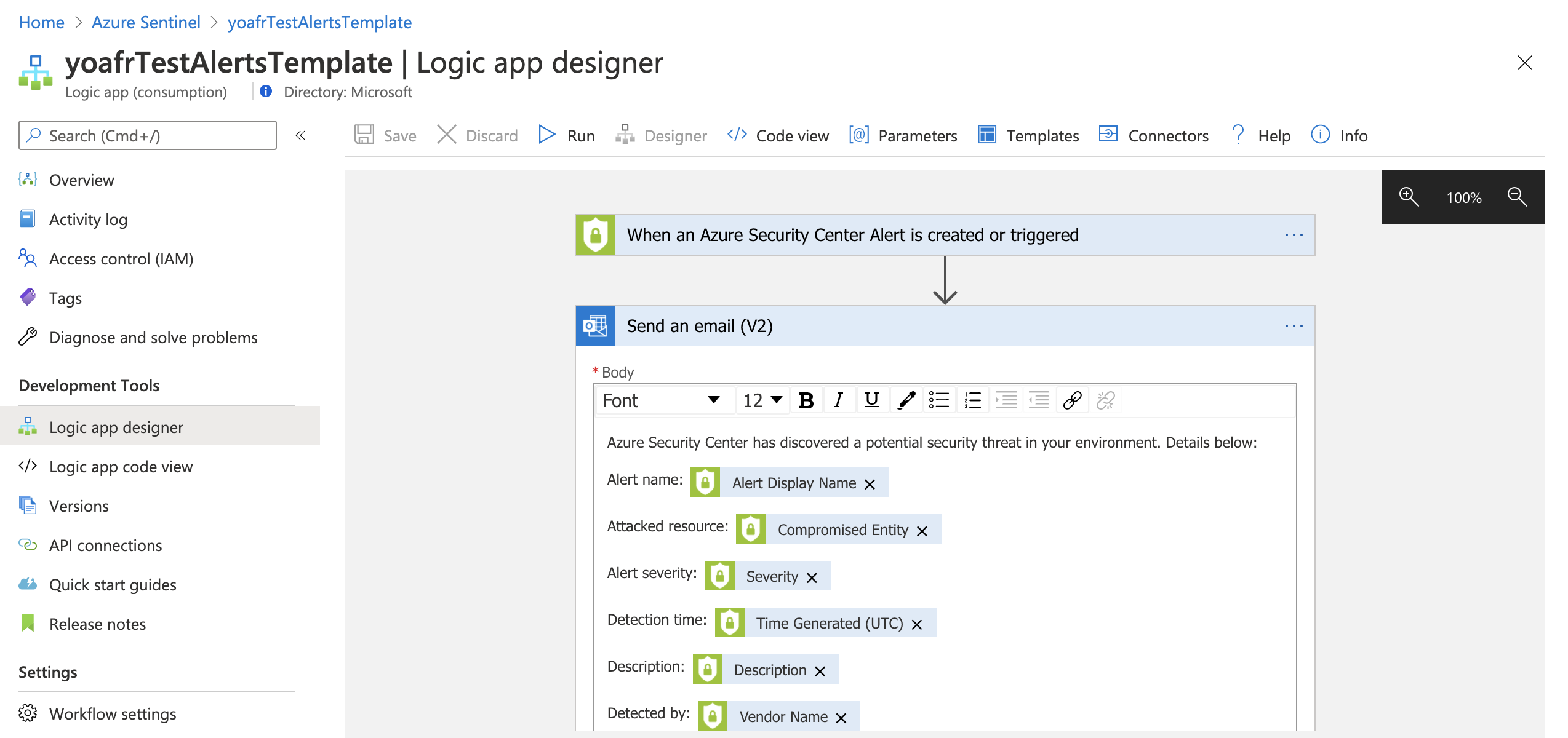
Automation playbooks
With the ability to respond to incidents automatically, you can automate some of your security operations and make your SOC more productive. Microsoft Sentinel integrates with Azure Logic Apps, enabling you to create automated workflows, or playbooks, in response to events. This functionality could be used for incident management, enrichment, investigation, or remediation. These capabilities are often referred to as security orchestration, automation, and response (SOAR).
When to use Microsoft Sentinel
Microsoft Sentinel is a solution for performing security operations on your cloud and on-premises environments.
Use Microsoft Sentinel if you want to:
- Collect event data from various sources.
- Perform security operations on that data to identify suspicious activity.
Security operations could include:
- Visualization of log data.
- Anomaly detection.
- Threat hunting.
- Security incident investigation
- Automated response to alerts and incidents.
Microsoft Sentinel offers other capabilities that could help you decide whether it's the right fit for you:
- Cloud-native SIEM. There are no servers to provision, so scaling is effortless.
- Integration with the Azure Logic Apps service and its hundreds of connectors.
- Benefits of Microsoft research and machine learning.
- Key log sources provided for free.
- Support for hybrid cloud and on-premises environments.
- SIEM and a data lake all in one.
When you began investigating Microsoft Sentinel, your organization had some clear requirements:
- Support for data from multiple cloud environments
- Features and functionality required for a security operations center (SOC), without too much administrative overhead
You've found that Microsoft Sentinel could be a good fit. It offers data connectors for syslog, Amazon Web Services (AWS), and other sources, and the ability to scale effortlessly without provisioning servers. During your analysis, you also realized that your organization should make automation a key part of its SOC strategy. Automation wasn't something the organization had considered before, but now you'll look into using automation playbooks.
If you're collecting infrastructure or application logs for performance monitoring, consider also using Azure Monitor and Log Analytics for that purpose.
And perhaps you want to understand the security posture of your environment, make sure that you're compliant with policy, and check for security misconfigurations. If so, consider also using Azure Security Center. You can ingest Security Center alerts as a data connector for Microsoft Sentinel.
Microsoft Sentinel can meet the requirements of the SOC analyst's organization:
- Support for data connectors for cloud and hybrid services.
- Features and functionality that you need, with minimal administration.
You explored what a SIEM solution is, and what Sentinel and its key components have to offer. Use Microsoft Sentinel and when other Azure products might complement Microsoft Sentinel to improve the security of your environment.
For more information contact us today...
Click Here, to Schedule a Free Consultation Or fill in the form below for a callback.